If your site gets hacked, it can absolutely be recovered and secured. At Wemaxa, we understand how stressful a breach can be, but with the right response, your site can be fully cleaned, restored, and protected from future attacks. The key is to act quickly the faster we address the issue, the better we can contain any damage and begin restoring normal operations.
We offer both guided support and full-service recovery depending on your needs. If you prefer to be hands-on, we’ll walk you through each step from isolating the problem and removing malicious code to restoring backups and applying critical updates. If you’d rather let us handle it entirely, our team will take over and manage the entire process, keeping you updated as we work.
🛠 If We Built or Maintain the Site
We can:
- Immediately scan and clean infected files
- Restore from backup (ZIP + SQL you already have)
- Set up hardening rules, 2FA, and bot protection
- Prevent re-entry by fixing the exploited vulnerability
The recovery process includes scanning for vulnerabilities, removing unauthorized files or code, repairing affected content, and restoring the site from a clean backup if necessary. We also identify how the breach occurred, whether through outdated plugins, weak credentials, or server misconfigurations, and take steps to patch those entry points.
📋 Optional Hardening Add-Ons
| Feature | Description |
|---|---|
| 🔐 Two-Factor Authentication | Add 2FA to all admin logins |
| 🧱 File Permissions Audit | Ensure correct chmod settings |
| 🔄 Auto-Core Updates | Keep WordPress and plugins up to date |
| 🔍 Live Activity Monitor | Track login attempts, file changes, logins |
Once your site is back online, we implement stronger security measures to prevent future attacks. This may include firewall setup, user access reviews, plugin audits, and regular security scans. At Wemaxa, we don’t just fix what’s broken we help you build a safer, more resilient digital presence moving forward.
🔥 What Happens When a Site is Hacked
| Symptom | What It Means |
|---|---|
| 🛑 Site is defaced or offline | Files or database modified |
| ⚠️ Redirects or popups | Malicious code (JavaScript, iframes) inserted |
| 🦠 Unknown files appear | Backdoors, phishing pages, or malware present |
| 📉 Traffic drops or SEO warnings | Google flagged the site as compromised |
| 🚫 Hosting suspended | Host detected malware or spam |
✅ Immediate Steps to Take
- Change all passwords
- WordPress admin
- FTP/SFTP
- Database
- Hosting account
- Scan your site
- Use Wordfence or MalCare for WordPress
- Run ClamAV on the server (you already have it installed)
- Check files and folders for recent changes
- Check for unauthorized users or plugins
- Remove unknown admin accounts
- Disable suspicious plugins or themes
- Restore from a clean backup
- If available, revert to a version before the hack
- Clean your database if it’s been injected with spam
- Notify your host (optional but helpful)
- They may provide logs, quarantine infected files, or give advice
🛡️ After Cleanup: Secure the Site
MORE LINKS:
Who owns the website
Transfer to a new host
Credentials recovery
AI for content generation
Analytics and tracking
SEO tools
Privacy policy
What if I don’t like it?
Reselling or licensing
PROTECTING YOUR WEBSITE AGAINST HACKING
What If My Site Gets Hacked?
At Wemaxa.com, we recognize that cybersecurity threats are among the most critical concerns for modern web applications, e-commerce platforms, and digital services. Despite best practices, even the most secure websites can be vulnerable to attacks ranging from brute force intrusions, SQL injection, cross-site scripting (XSS), malware infections, to more sophisticated zero-day exploits. In the unfortunate event that your website experiences a security breach or unauthorized access, we have a comprehensive response framework designed to mitigate damage, restore functionality, and reinforce security protocols. Our incident response strategy begins with immediate detection and containment, leveraging monitoring tools, firewall logs, intrusion detection systems (IDS), and security analytics from trusted providers such as Cloudflare and Sucuri. This allows us to quickly identify compromised accounts, malicious code injections, or abnormal activity patterns, minimizing exposure to sensitive user data or intellectual property. Our team then conducts a thorough forensic analysis to determine the origin, scope, and nature of the breach, documenting every step to ensure compliance with legal and regulatory obligations and to prevent recurrence. In parallel, we initiate immediate remediation procedures, which may include purging malicious scripts, restoring files from secure backups, updating all vulnerable components such as WordPress core, plugins, themes, and database credentials, as well as implementing enhanced access control measures.
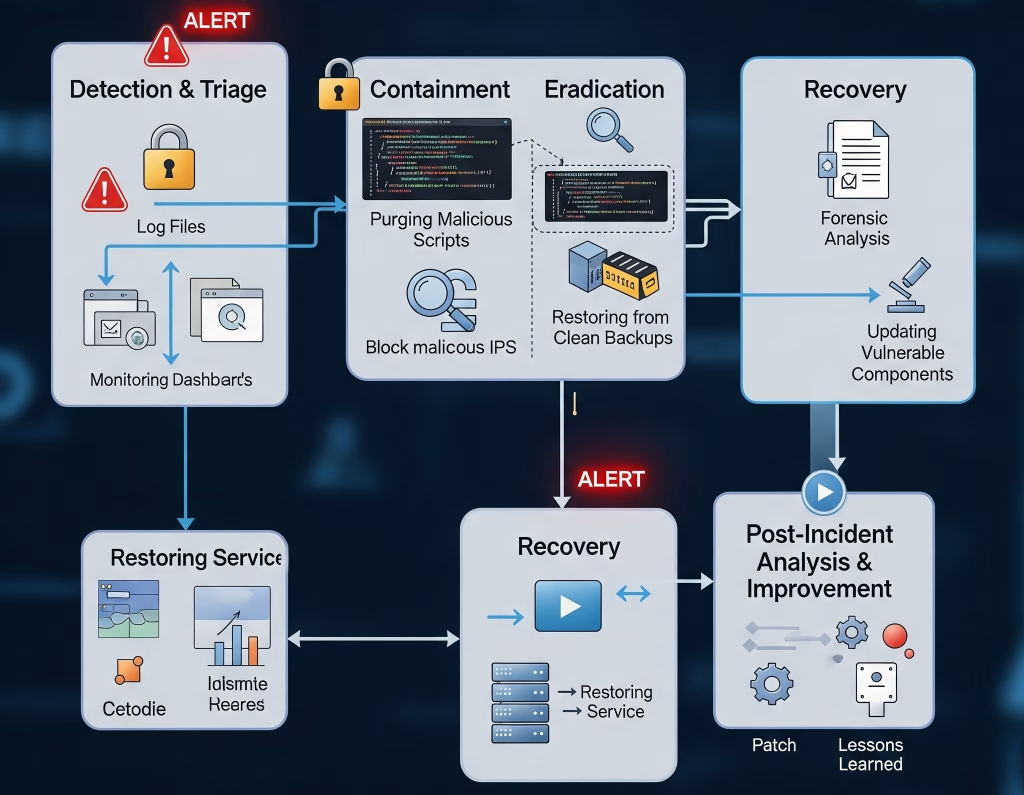
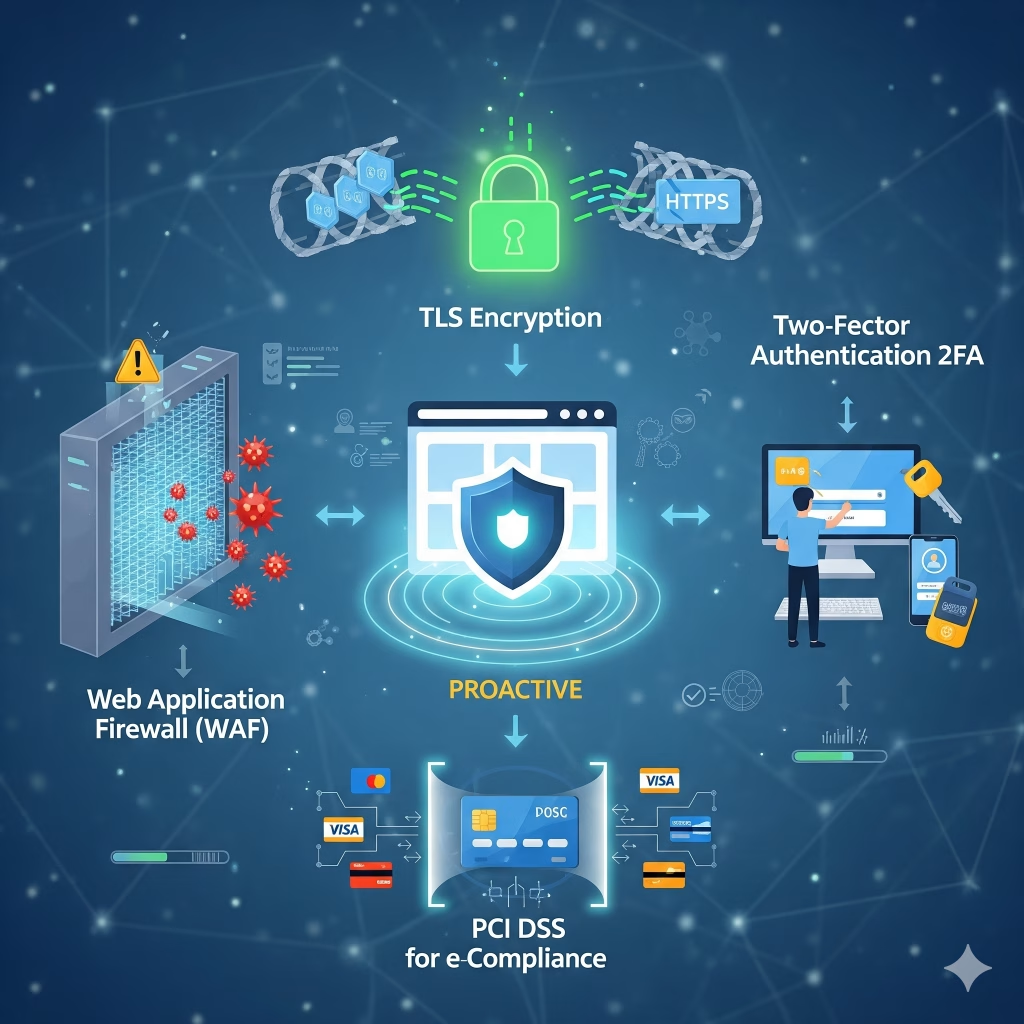
Beyond immediate remediation, Wemaxa emphasizes proactive security reinforcement to prevent future incidents. This includes configuring advanced server-side protections, deploying Web Application Firewalls (WAF), enforcing TLS encryption for all data in transit, and implementing robust authentication mechanisms including two-factor authentication (2FA) and IP whitelisting for administrative access. Our security audits also cover database hardening, privilege separation, and continuous monitoring of server integrity using automated tools and manual inspection. For clients who rely on e-commerce capabilities, we integrate Payment Card Industry Data Security Standard (PCI DSS) compliant workflows to ensure that financial transactions remain secure even if the front-end experiences a compromise. Additionally, we provide clients with actionable guidance on user password policies, session management, and safe coding practices to reduce vulnerabilities from human error or weak credentials. By collaborating with industry authorities such as OWASP and following up-to-date threat intelligence feeds, Wemaxa maintains a security posture that aligns with international standards, best practices, and the evolving cyber threat landscape.
| Action | Tool or Method |
|---|---|
| ✅ Firewall & malware scanning | Wordfence, Sucuri, or server-level rules |
| ✅ Block malicious IPs | Fail2Ban, Cloudflare, or server firewall |
| ✅ Plugin/theme hardening | Remove unused code, install only trusted ones |
| ✅ Core file integrity monitoring | Enable in Wordfence or set up file watchers |
| ✅ Regular backups | Daily/weekly site + database backups |
| ✅ Email alert system | Get notified of login attempts or file changes |
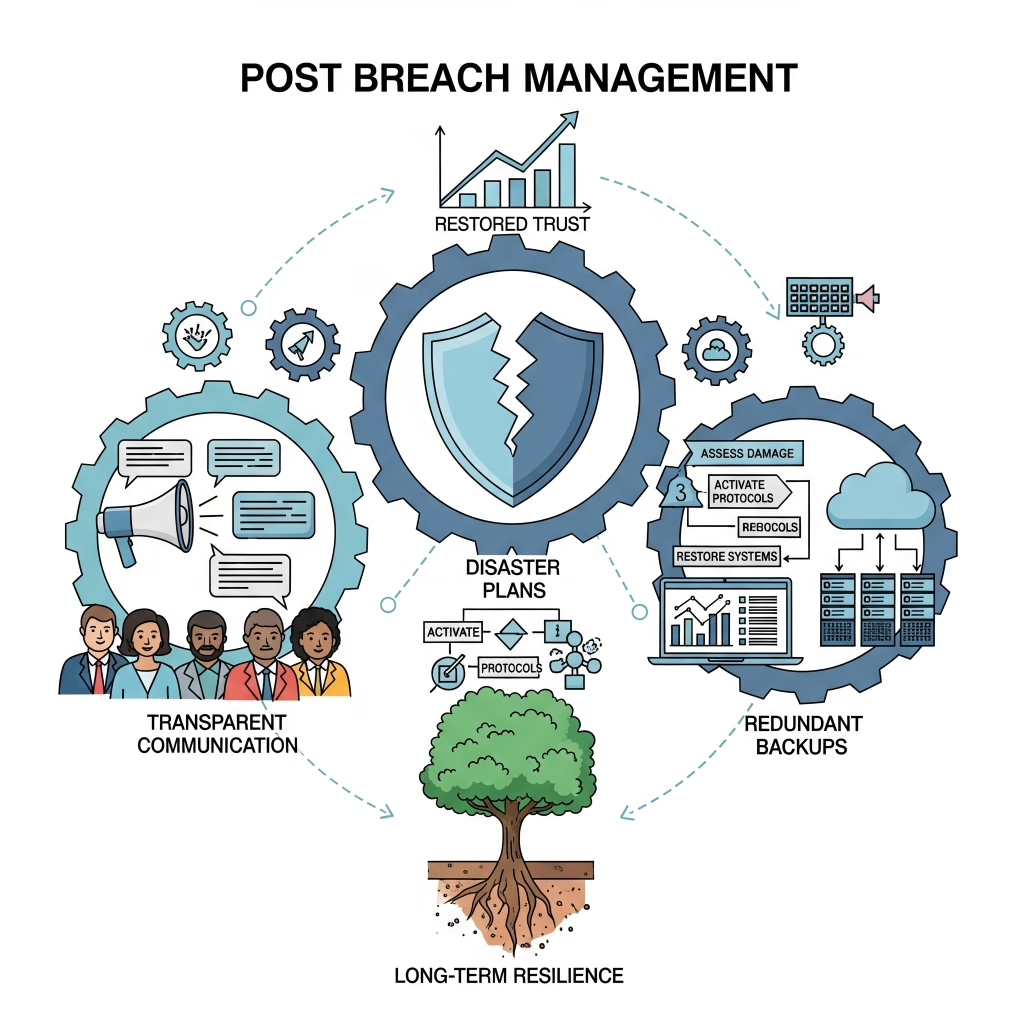
In the aftermath of a hack, restoring trust with your users and clients is paramount. Wemaxa assists with transparent communication strategies, providing logs, incident reports, and actionable recommendations for affected stakeholders. Our services include automated website scans, real-time monitoring dashboards, and vulnerability alerts that integrate with client notifications, ensuring that any potential future compromise is detected and addressed before significant damage occurs. For businesses with regulatory requirements such as GDPR, CCPA, or HIPAA, we ensure that breach notification timelines, data handling procedures, and reporting obligations are strictly followed, mitigating legal risk while safeguarding your brand reputation.
Additionally, we guide clients on implementing disaster recovery plans, redundant backups, and failover systems so that, even under extreme conditions, website downtime is minimized and critical functionality remains accessible. Wemaxa’s holistic approach to post-breach management combines immediate technical intervention, strategic preventive measures, legal and compliance alignment, and long-term system resilience to create a secure and trustworthy digital presence. For more insights on preventing hacks and implementing robust security measures, visit Wemaxa Security Services and refer to the OWASP Security Guidelines.
Ultimately, while no system can claim absolute immunity from hacking, partnering with Wemaxa ensures that your website is equipped with advanced protection, rapid incident response, continuous monitoring, and comprehensive recovery protocols. Our focus is on not only restoring sites quickly after an incident but also educating clients and implementing cutting-edge defenses to prevent recurrence, making security a foundational component of your long-term digital strategy. By integrating best-in-class cybersecurity practices, leveraging expert monitoring, and maintaining proactive updates for all software components, Wemaxa positions your business to operate with confidence, minimizing both financial and reputational risks associated with online attacks while ensuring compliance with modern cybersecurity standards.


