If your site is ever compromised, Wemaxa will respond immediately to secure, clean, and restore it. We treat security incidents with urgency and care, activating our recovery protocols the moment an issue is detected or reported. Our team works swiftly to contain the breach, remove malicious code or unauthorized access, and restore your website or application to a stable, safe state.
The first step is to lock down the affected system, isolate any vulnerabilities, and perform a complete scan to identify the source of the attack. We then clean the infected files, verify the integrity of your database and content, and restore your site from a secure backup if needed. Our goal is to get you back online as quickly as possible while ensuring no remnants of the threat remain.
✅ Ongoing Monitoring Setup
- Uptime monitoring + intrusion alerts
- Set up daily scans, firewall logs, and login attempt tracking
- Auto-block bots, brute-force attempts, and suspicious IPs
After the immediate recovery, we conduct a full review of your website’s structure and hosting environment to understand how the attack occurred. We then implement security patches, update software, strengthen access controls, and, if necessary, adjust firewall and monitoring settings to block similar threats in the future. Every fix is documented so you stay informed throughout the process.
📋 Client Support Options After Recovery
- Free cleanup if you’re on a support/maintenance plan
- One-time malware removal & hardening (hourly or flat fee)
- Option to subscribe to a security retainer with:
- 24/7 monitoring
- Weekly audits
- Immediate threat mitigation
🚨 If Your Site Gets Hacked: Here’s What Wemaxa Does
✅ 1. Emergency Response & Isolation
- We take the site offline temporarily or move it to a secure staging area.
- Block external access while retaining backend admin entry.
- Audit recent activity, file changes, and access logs.
✅ 2. Malware Removal
- Scan your entire site with tools like:
- ClamAV, Wordfence (for WordPress), RKHunter
- Identify and delete:
- Injected scripts
- Malicious plugins or files
- Suspicious admin accounts
✅ 3. Restoration from Clean Backups
- If backups are enabled:
- Restore the most recent clean version.
- Patch vulnerabilities before relaunch.
- If no backups exist:
- Manual cleaning and forensic recovery is performed.
✅ 4. Security Hardening
- Update all core files, plugins, and themes
- Change all passwords (FTP, admin, database)
- Lock down file permissions (chmod, chown)
- Disable XML-RPC, unused services, and expose headers
- Install or reconfigure:
- Web application firewalls (WAF)
- Fail2Ban
- 2FA for admin access
MORE LINKS:
Maintenance services
Support packages
If something breaks
Monthly fee
Site migration
Backups
Bug reporting
New features
Support channels
WHAT IF MY WEBSITE GETS HACKED?
At Wemaxa, we recognize that having your website compromised can be a critical and highly stressful event, potentially resulting in lost revenue, damaged reputation, decreased user trust, and long-term SEO impact. Cyberattacks can occur for a variety of reasons, including outdated software, insecure passwords, vulnerable plugins, or malicious third-party scripts. To address these risks, Wemaxa provides a comprehensive website hacking response and recovery service designed to quickly identify, contain, and remediate any breach. Our proactive and structured approach ensures that your website can be restored securely while implementing safeguards to prevent future incidents.

The first step in our response process is rapid containment of the affected environment. Upon detecting suspicious activity or a confirmed hack, we immediately isolate the compromised system to prevent further unauthorized access, data theft, or site defacement. Depending on the severity of the breach, this may involve temporarily taking the website offline, moving it to a secure staging environment, or restricting administrative access. During this phase, we perform an in-depth analysis of server logs, file modifications, database activity, and traffic patterns to determine the source and extent of the compromise. This detailed forensic assessment is essential for developing an effective recovery plan and for ensuring that no hidden vulnerabilities remain.

Once containment is achieved, Wemaxa conducts a comprehensive malware and vulnerability sweep. Using advanced security tools such as Wordfence, ClamAV, RKHunter, and custom scripts for full-stack environments, we scan all files, plugins, themes, and databases for malicious code, backdoors, injected scripts, or unauthorized admin accounts. We also examine configuration files, cron jobs, and any connected APIs or third-party services to identify potential vectors of attack. By thoroughly cleansing the system, we ensure that all traces of malware or hacking attempts are eradicated, which is critical to preventing repeat compromises.
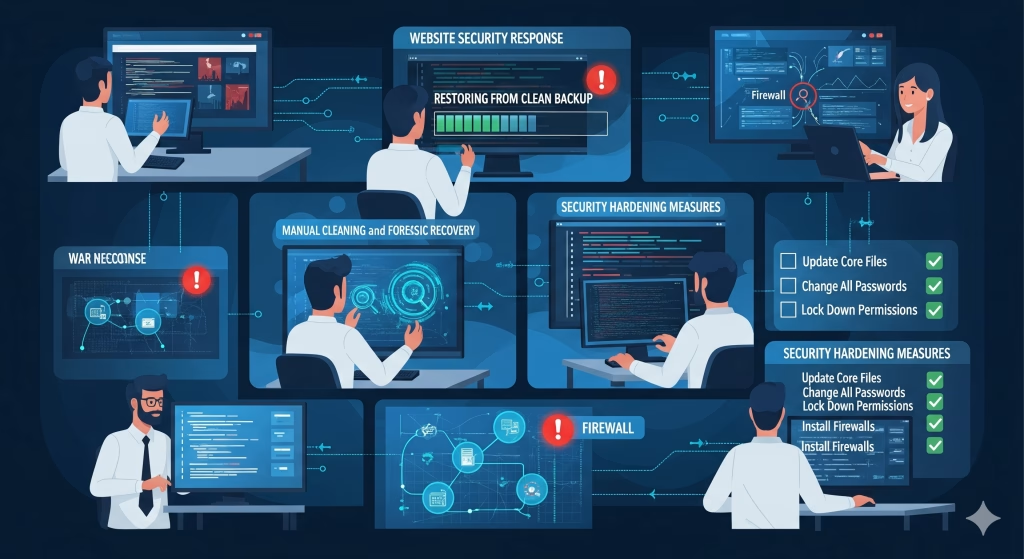
After completing the cleanup, we restore the website to its most recent secure state using verified backups, if available. Wemaxa ensures that backups are thoroughly tested before restoration to avoid reinjecting any compromised files or configurations. If no recent backups exist, we perform a meticulous manual recovery, reconstructing the website’s structure, files, and database while validating functionality and content integrity. This process includes repairing broken links, restoring media assets, verifying forms, and re-establishing API connections. Every restoration is followed by rigorous quality assurance to confirm that the website operates as intended across all devices and browsers.
Security hardening is the next critical phase. Wemaxa implements a multi-layered defense strategy to protect your site from future attacks. This includes updating core software, themes, and plugins to the latest stable versions; changing all passwords, including FTP, admin, and database credentials; configuring strict file permissions; and disabling unused services. We integrate Web Application Firewalls (WAF), enforce Two-Factor Authentication (2FA) for all administrator accounts, and deploy automated monitoring to detect suspicious activity in real-time. Additionally, we guide clients on implementing best practices such as regular backups, timely updates, and secure user management protocols. Resources like US Cybersecurity’s Hacked Website Guide and Google’s Webmaster Guide for Compromised Sites provide further insights into long-term site security strategies.
Finally, Wemaxa emphasizes continuous monitoring and post-incident reporting. After your website is restored and secured, we maintain vigilant oversight to ensure no residual threats remain and to quickly address any anomalies. Our reports detail the actions taken, vulnerabilities resolved, and recommendations for ongoing protection. By choosing Wemaxa, you are not only receiving immediate remediation for hacked sites but also a long-term partner in website security, performance optimization, and resilience, allowing your business to operate confidently in an increasingly complex digital landscape.
At Wemaxa, we believe in not just fixing the issue but also fortifying your platform against future risks. Our clear protocols and proactive defense strategies help reduce the chance of repeat incidents, giving you peace of mind and a stronger, more resilient digital presence.


